
PROTECTING YOUR BUSINESS FROM CYBER THREATS

Samira Kabbour
CMO
Posted by Jim Carnes
It’s Friday afternoon (it always happens on Friday afternoon) and the phone rings — there’s a breach. Your internet provider has called and malware associated with the latest botnet has been detected coming from your corporate network. The incident response plans are triggered and everyone goes into high alert, looking for the source.
The common thought trajectory goes something like: How could this happen? We use the latest and greatest security products. Did someone open a phishing email? Did a hacker breach our firewall or was a vendor compromised? There goes my weekend.
How can we stop fearing that Friday afternoon call?
Integrating security into each aspect of your business could mitigate this stressor. When people, processes, inventory and technology are coordinated, the fear and uncertainty of security breaches is replaced with straightforward and seamless responses that protect your Friday evening dinner plans.
Business security
The conversation should always begin with your business. You need to understand the processes, the people and the vendor and partner relationships. Understanding how the critical aspects of the company function and interact will often point to gaps in security.
Consider how vendors deliver invoicing, how employees collaborate and how development processes are executed. It is important to understand these (and any other) processes as your data, and therefore your data exchanges, are occurring in locations and ways of which you may be unaware. When was the last time you asked your accounting or manufacturing departments how they share data? The answers — or lack thereof — may be surprising.
Key components to consider
Are the tools that facilitate secure business processes in place? Look for:
- Single-sign solutions to ease integration of people and technology
- Multi-factor authentication solutions that ease the password management burden on users (compromised passwords are responsible for nearly half of organizations that are breached according to the 2017 Verizon DBIR)
- Product suites that integrate business processes and technology solutions
- Secure supply chains that enumerate the risks to both hardware and software solutions while protecting them (a white paper published by the SANS Institute offers guidance on combating supply chain cyber risk)
Solution security
Whether your business is delivering software, hardware or services, the development of those solutions include security from the start. The ability to clearly articulate the purpose of the system, how it will be used, who will be using it and what value it provides will help begin the conversation. Articulating these key factors will help define the threat environment, the adversaries and the controls necessary to mitigate the attacks. Mitigations will therefore have context and be able to address real threats, rather than generic ones.
The best security solutions are often lost during implementation.
The 2017 Ponemon Cost of a Data Breach Study details as an example that U.S.-based financial industries that suffer a breach will, on average, spend $11 million per breach. Including the suggestions below can help reduce the cost by as much as $3 million. The key is knowing and planning for a business’s unique risks.
Know your threat
There are a number of threat models and methodologies published. While some are detailed and comprehensive, others begin by asking simple questions to guide thought processes. As an example, DREAD attempts to quantify risk based on threat. The Open Web Application Security Project (OWASP), a nonprofit organization focused on software security, publishes guidance on software-centric models; many of them are useful for non-software solutions, as well.
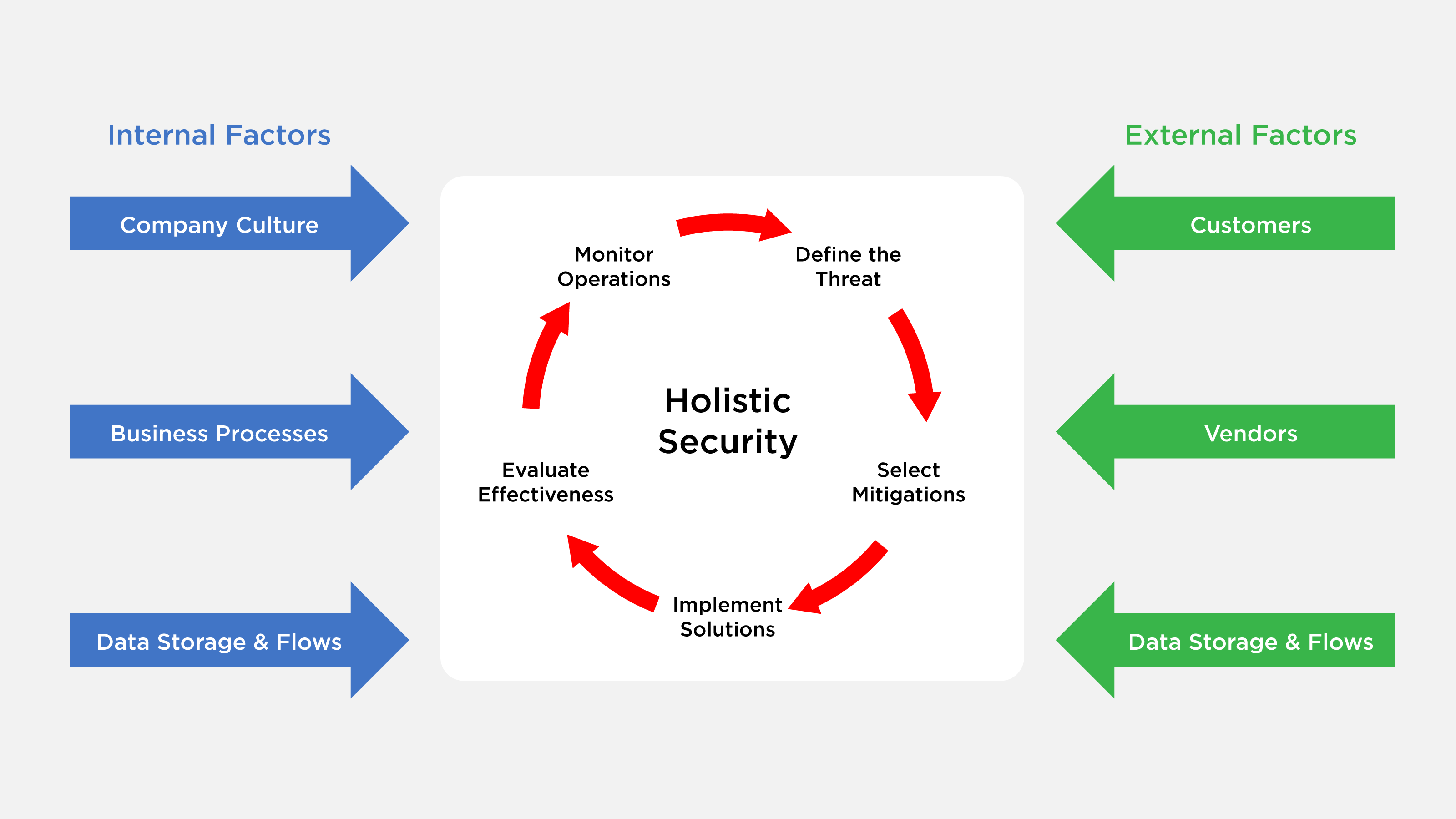
Selecting your controls
Once there is an understanding of the threat(s), the appropriate mitigation controls can be selected. There are a number of methodologies for selecting controls; NIST has published SP 800-53, and while it focuses on systems for U.S. federal government use, its guidance is useful outside of federal systems. Additionally, the Center for Internet Security publishes hardening guidelines and recommendations for securing solutions.
Implementing security
The best security solutions are often lost during implementation. Feature requests, timelines and bugs will complicate the best laid plans. It is critical that security is integrated during the development and implementation of your solution(s). Keep track of projects — effective version controls, source code protections and secure collaboration of team members must be considered.
Designing and developing solutions securely matter very little if deployment is poorly managed.
The development team will no doubt have its preferred selection of tools, but ensuring you are tracking each facet of development is important. Tools such as Jira for feature and bug tracking, Git for version controls and Slack for collaboration are all viable solutions. The key is to recognize that these tools will contain critical information that, if compromised, could damage security.
Evaluating security
Testing solutions for weaknesses is a critical piece of holistic security. Suites such as Tenable’s Nessus security scanner can test for known vulnerabilities and compliance violations against a wide variety of operating systems and applications. Both dynamic and static analysis tools can be used to test software for security flaws.
Deploying security
Designing and developing solutions securely matter very little if deployment is poorly managed. The challenge facing technology today is that the hosting environment is constantly changing. Where you deploy a solution — be it to a physical server, a virtualized server or a cloud hosting solution — influences the threat, and, by extension, the solutions. It becomes incumbent upon the business to build up the entire service stack to best practices, review service providers’ security compliance and controls and disseminate the visibility and response plans to be used in the event of a breach.
When data is stored in the “cloud,” it is simply being moved to someone else’s system. That system needs to be vetted appropriately.
Monitoring
Continuous monitoring is the goal to strive for. But what does that really mean? What is being continuously monitored? Is it the hardware, the operating systems, the database, the web application, the data repositories and all the data flows? In short, yes — it’s everything. The challenge is how to monitor the entire service stack effectively.
When considering and prioritizing solutions in this space, focus first on what is most critical and move out from there. Detecting data flow anomalies should be the first priority, followed by services exposed to untrusted entities and inward from there. Keep an eye on more than just the external interfaces; should alerts fail to trigger a breach on an external interface, your internal monitoring is the last line of detection and defense. Centralizing alerts for end-to-end monitoring will help prepare for the next generation of security — automated defenses.



